Increasing Web Security in 2022 with CloudFlare Pages
Introduction
As I relaxed on my annual trip to Noosa, QLD, I read a linkedin post, from the state of WA, highlighting the state of web security during our last Australian Federal Election cycle.
The Challenge
Now I didn’t have a laptop with me, however I thought I’ll seee what I can achieve with an iPhone and a chromebook which I had with me.
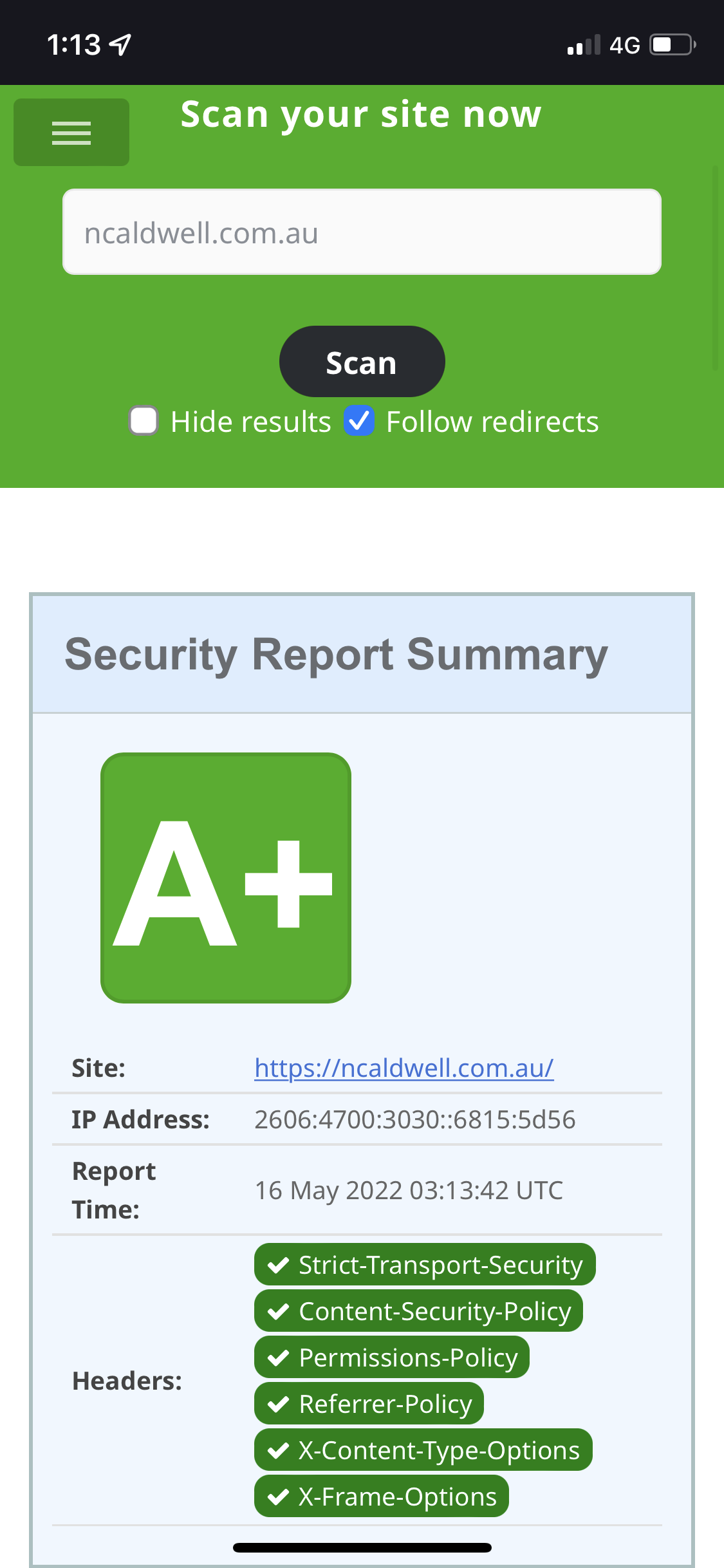
Firstly, I checked my website (this blog) with the following results.
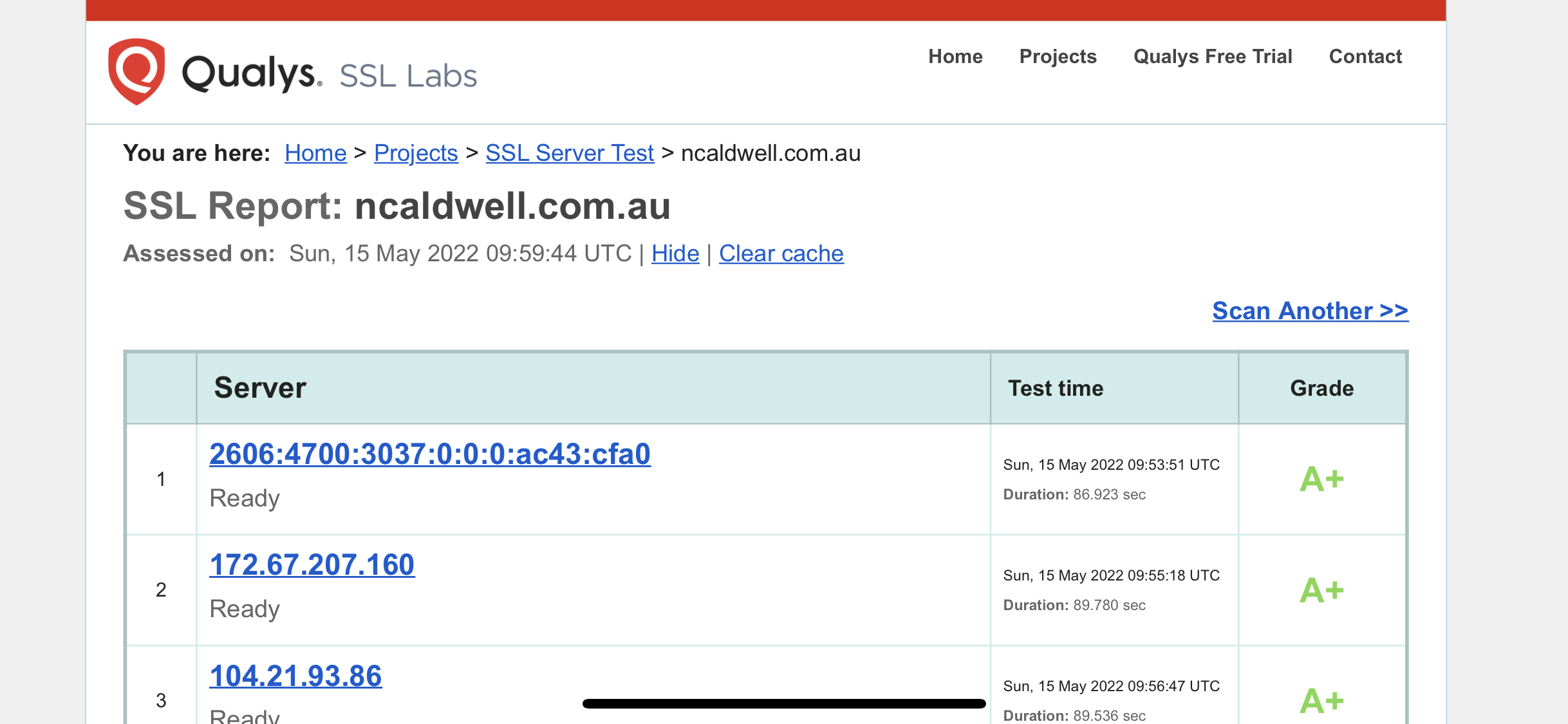
Fortunately, I had enabled DNSSEC when I setup my blog with cloudflare, so grade A from ssllabs.
Security Headers with CloudFlare Workers
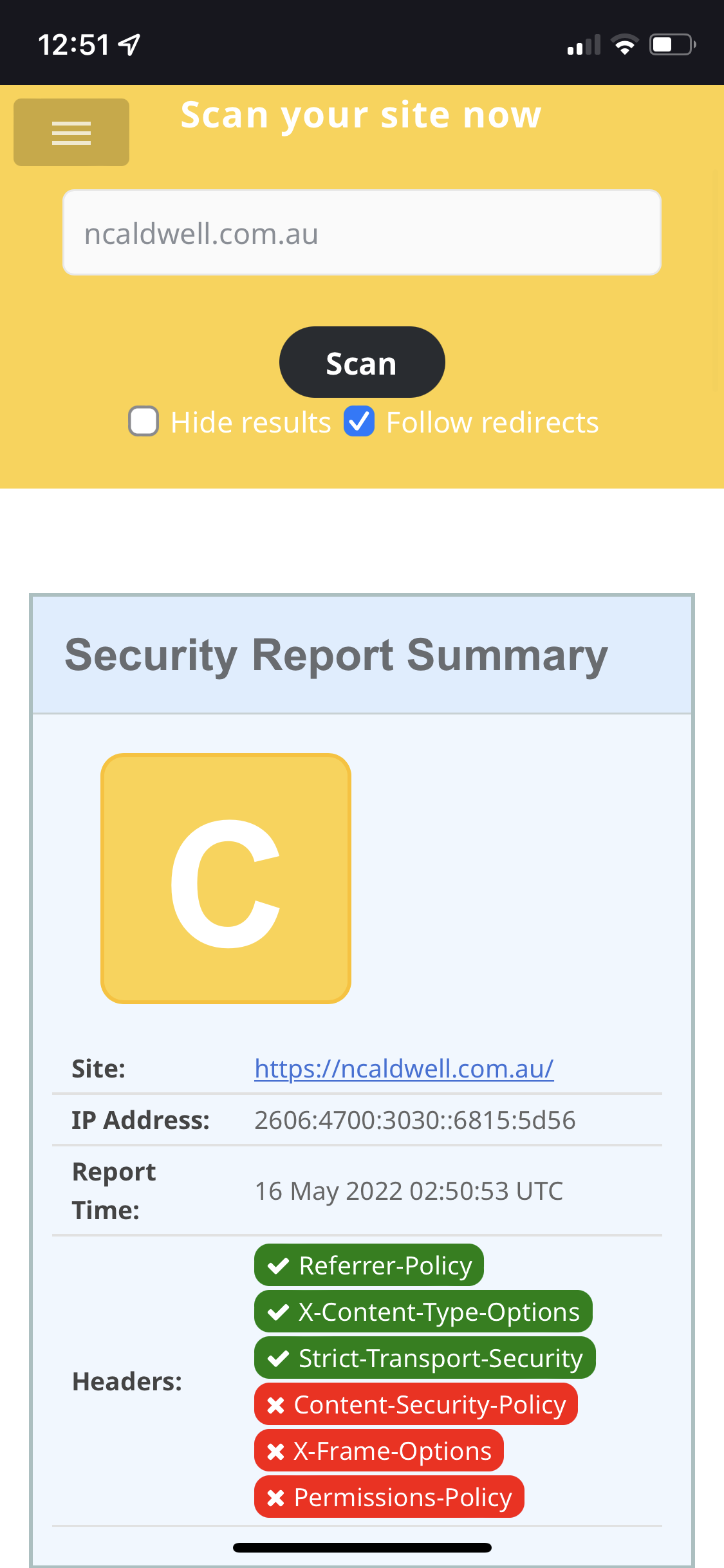
However, I had not ventured into the security headers side of things as yet. I have setup a lambda edge site, meshing with cloudflare, so I investigated cloudflare workers to achieve the same.
Now my site is returning a much higher score from Scott Helm’s SecurityHeaders.com.
Conclusion
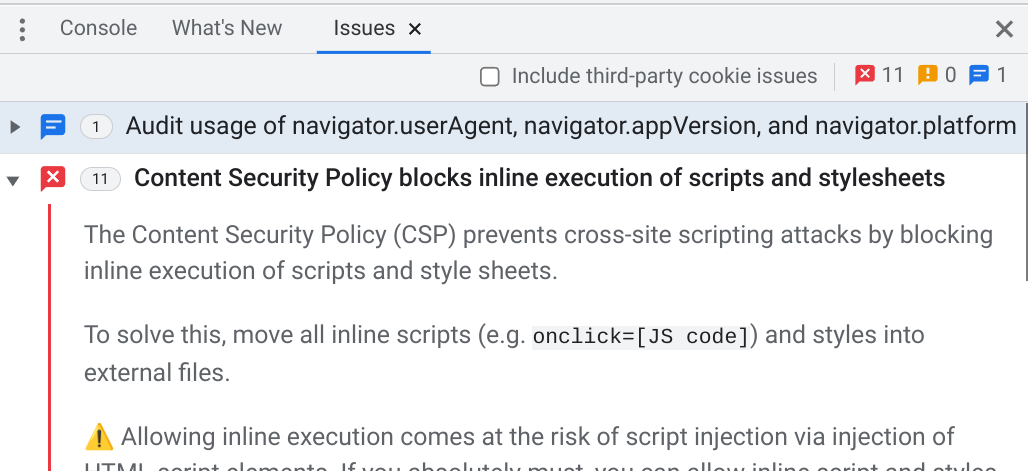
However, javascript was not happy, I didn’t think much javascript was involved in my blog, however the google translate function had identified a number of domains to be trusted. I added those to the security policy, and ended up with plenty, such as:
- content-secuirty-policy: default-src ‘unsafe-inline’ ‘self’ www.gstatic.com www.google.com translate-pa.googleapis.com translate.googleapis.com cdn.jsdelivr.net cdn.countryflags.com cloudflareinsights.com *.cloudflareinsights.com translate.google.com cdnjs.cloudflare.com ncaldwell.com.au *.ncaldwell.com.au
AI
I’ll leave you now, with some content from my new robot, copy.ai
Throughout my career, I’ve seen a few trends in web security. For example, we used to worry about hackers and malware that would infect our computers, but now we worry about fake news and online privacy. And yet, those threats are still out there! In the past year alone, we’ve seen email hacks on politicians’ accounts and identity theft scams involving Amazon Echo speakers and Google Home speakers—and these haven’t even been around for 20 years. So what’s next? Will technology solve these problems or make them worse? Let’s take a look at what’s coming down the road for web security in 2022:
In a perfect world, TLS would be completely automated. That is to say, it should be possible to encrypt all traffic that passes between two applications without any user interaction. The two applications could negotiate an encryption protocol and key in the background without any user input required. This can be accomplished by using an API like Let’s Encrypt which issues certificates automatically based on requests from clients.
No matter what happens, we will always have some amount of manual work involved with TLS configuration. However, this manual work will only be needed when upgrading or changing TLS configurations or when making sure private keys are properly backed up (in case of key rotation).
AI will detect many cyber threats before they happen.
Artificial intelligence (AI) is a technology that can detect and stop threats in their tracks before they have a chance to cause harm. AI-assisted security solutions are already more effective than human detection systems, as they are able to detect threats that are not yet known, have not yet been seen and have not yet been created. In 2022, the use of AI will become so widespread that traditional intrusion detection and prevention systems will be rendered obsolete by this new technology.
The widespread adoption of AI-based security tools will come at no cost to the user and will make cybersecurity a reality for everyone—whether they’re an individual user or large enterprise organization.
Most small sites won’t use HTTPS.
If you’re not a security expert, you may be wondering why we should care about this.
The majority of sites on the internet are small or medium-sized—many are one-person operations. They don’t use HTTPS for a number of reasons:
It’s too expensive. Encryption adds latency and CPU cycles, which means page load times will be slower and users will get annoyed and stop coming back to your site (or even leave your site altogether).
They don’t want to deal with it. Many people who run small sites can’t afford to hire someone with knowledge of SSL/TLS certificates, let alone someone that can configure their server correctly so that they can take advantage of them without breaking anything else on their machine or network.
They don’t think it matters much because they have nothing important on their website anyway (and if they did have something important then it would still be secure because they’re using HTTPS).
Many large sites won’t encrypt with the best protocols and ciphers.
Many large sites won’t encrypt with the best protocols and ciphers.
You might have noticed that some websites still don’t use TLS, or are using older versions of TLS (1.0, 1.1), or aren’t using forward secrecy. Some sites also don’t use perfect forward secrecy (PFS), which is a more recent form of encryption that ensures that even if an attacker were to gain access to your keys, they wouldn’t be able to decrypt all past communications.
That’s not good enough for us though—CloudFlare utilizes the latest versions of protocols like TLS 1.3 and PFS. We want our users’ connections to be as safe as possible, so we’re always looking into ways we can make them safer while still providing value-added services like caching and CDN support at no extra cost!
Trends in technology don’t eliminate the need for basic security measures on websites.
The answer is simple: security holes are everywhere. The more a website has to do, the more security holes it has. Obviously, this includes all websites that host payment information or personal data like email addresses. However, even sites that don’t have to deal with sensitive information still need basic security measures in place to protect against common threats like brute force attacks and hacking attempts.
The problem is that these basic precautions can be difficult for smaller companies who don’t have dedicated IT resources or developers on hand to monitor their sites’ performance constantly. And while larger companies often have these resources available—and larger budgets to spend on securing their sites—they’re often still vulnerable because they aren’t aware of how important basic web security is when dealing with threats like DDOS attacks or other types of cyberattacks where hackers aim at bringing down entire networks rather than individual websites (such as what happened recently when Cloudflare’s DNS servers were taken offline by an unknown attacker).
AI Conclusion
Overall, the future of security is looking brighter than ever. There are still ways that you can protect your website today, even if it doesn’t seem like much will change in 2022. The best way to ensure that your site is ready for tomorrow’s threats is by keeping an eye on what’s happening now—and taking steps now that will help keep your site secure tomorrow (and beyond). Also a big thanks to copy.ai for authoring this page!