AWS mini project -Serverless App - Pet-Cuddle-O-Tron
Introduction
Leaning towards serverless applications, over VMs, then containers, and now server “less”, mainly in terms of less servers for me to manage, someone manages them of course :)
Today I’ll be implementing a simple serverless application using S3, API Gateway, Lambda, Step Functions, SNS & SES.
Inspired again by Adrian Cantrill’s advanced mini project - Serverless App - Pet-Cuddle-O-Tron, highly recommended to look through his advanced demo projects, and his AWS course options available at learn.cantrill.io!
Stage 1
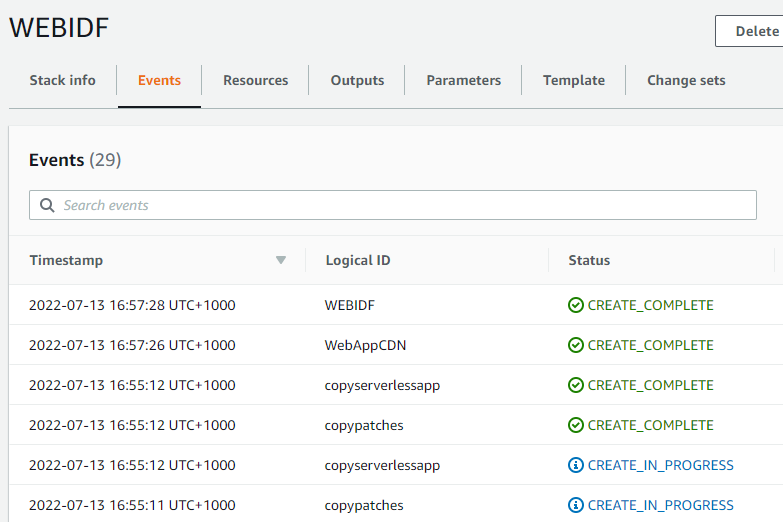
Ok, loading a simple YAML into cloudFormation, simple, just need a little time for cloudfront to become active. This one will be at https://d1quoeddwd14ae.cloudfront.net.
Stage 2
Ok, pointing a google project at cloudfront, this is where I’d like to start adding in my custom domain. As my domain is hosted in CloudFlare for DNS and Pages, a few extra steps will be needed to first generate an ACM certificate, then I can add my domain to cloudfront. For now, webapp will be used as a subdomain, adding the ACM CNAME without proxy in CloudFlare should do the trick.
Next, after a short walk with my dog, the ACM has been validated, so now CloudFront will allow me to add this domain, as I have proven ownership. Next to add my domain into google cloud project - “Authorized JavaScript origins”. I also updated the behaviour from HTTPS only, to redirect HTTP to HTTPS. webapp.ncaldwell.com.au
Stage 3
This is the cognito side of things, adding a policy from the cloudFormation stack to Cognito_WebApp_Auth_Role, straight forward.
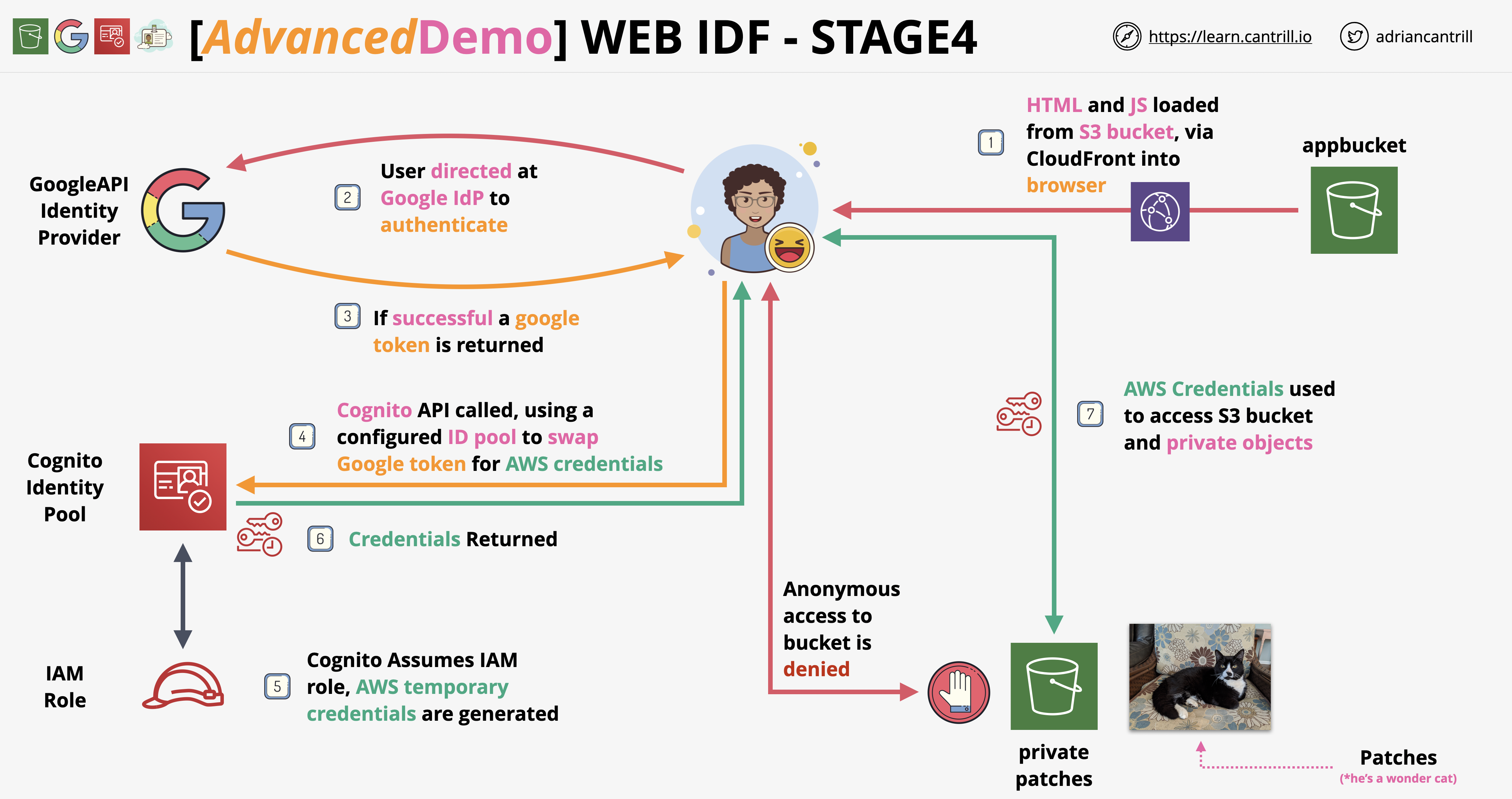
Stage 4
Download s3 files, one at a time to avoid a zip file. Move to a directory and open that directory with VS CODE. Adrian has clearly labelled what needs to be updated, so it’s a breeze to add the required IDs.
If you try your subdomain before adding it to cloudflare, like me, on windows go to a powershell prompt and run “ipconfig /flushdns”. If you have a bad DNS result, the quickest option is to try on another device. :)
Stage 5
Success!

Conclusion
A great demo and a great intro to having your own web identity federation, linking Google to AWS resources. Next I plan to add microsoft, all possible with cognito identity pools.